The following is a guide prepared by community member @Kruisdraad. I have helped clean up the English a little bit and posted it here in three parts.
Note that this is not an official Phala team item and is not a supported procedure. It is public info which some may want to try to mod their systems. It requires deep-level tinkering in ways that probably violate system warranties and may make your system permanently unbootable. I cannot and will not provide support to those who use it: try at your own risk.
If you’re willing to take on the risk for yourself, feel free to read on.
BIOS MCU Hack Mod
by Kruisdraad
Disclaimer
This document, even if well prepared, contains very dangerous changes to your systems BIOS and might brick your system. Although some systems have a BIOS that allows recovery if a firmware update is faulty, in some cases you can throw away your motherboard (CPU, RAM, HDD, etc. are not affected). You should not rush this and then slowly apply modifications and properly test it. The PHALA team does not provide support on this guide, does not support the process of editing the BIOS image, and cannot provide any support if you your BIOS is bricked. This document is just an effort to aid people with their BIOS problems who desire to take matters into their own hands. If your modified BIOS boots it does NOT mean it is working properly, your system might behave strangely… if you notice issues, install the original BIOS while you still can!
I (Kruisdraad) took a lot of time and effort into writing this, to support the community. I do not provide any support nor reply to PM’s. I could have kept this to myself, which would given me a nice advantage against the other miners, having one of the few Confidence Level 1 farms. But sharing this would improve the Phala network for everyone, so I’ve shared – if you use and extend the info here, share back!
This BIOS modifications guide COULD solve some problems, but not all of them. Do not complain if this guide does not work. The correct way to achieve these goals is to ask the motherboard/BIOS vendor to provide an update. Based on own testing on several motherboards and vendors it looks like about 80% of the issues could be fixed by following this guide (DO NOT SKIP STEPS!). Some vendors have special update tools which are not compatible with this guide. You might have to add your own wizardry!
Problem explained
So you are likely reading this because you don’t have a Confidence Level 1 miner, and really really really want one. You need to know a few things about the problem and the ideal conditions for getting a level 1 miner. There are several main criteria that need to be met:
- Having hardware that supports Intel SGX. This does not only mean the CPU, but also the motherboard. Not every vendor implements this or provide support on missing features. For example, in my experience, MSI never provided any good support, while ASRock did epic support. Even then most BIOSes don’t have any BIOS options for Intel SGX, because it takes time to implement it and is not used on a large scale. You will have to invest time and money testing boards to get the build that works for you. Note that if a (US based) build works for you, it might not work for another (e.g. EU builder) due to versions in hardware. Do NOT assume that it works because someone else said so, there are no shortcuts.
- Having the right SGX driver version. Intel releases new ones regularly to fix bugs and security issues. Keep in mind that the Phala scripts install the latest version at the moment of installation, but does NOT (yet) update them. In addition, you cannot simply update it. (hint: you must stop the EASMd service and docker containers, then run the uninstaller). To check the version you can issue ‘modinfo intel_sgx’ and look at the version indicator.
- Having the right SDK version. You can update this at any time, but again has to be update manually at this time. There is no good way to check its version, when In doubt … just reinstall again.
- Having up-to-date Intel Packages. During installation an Intel APT repository is added
- Having an up-to-date BIOS that includes the latest MicroCode Update (MCU). Note that when downloading a new version from e.g. MSI, it might be listed as the newest version released by the motherboard manufacturer… but it may not contain the latest MCU for the CPU.
- Having correct BIOS settings for your motherboard. This varies per vendor per board and requires persistence in checking each one of them, however a few common ones: Disable GPU, Disable Hyperthreading, Disable Virtualization, disable any overclocking, enabling Intel SGX, etc. You may spend countless hours into debugging this, there is no shortcut.
- Having good internet connection. No, it’s not about speed … it’s about connectivity to the Intel SGX IAS services, which play a major role in the Remote Attestation process. This might fail if you have packet loss, uneven bandwidth, or simply live in a place like China where the internet is filtered in many ways.
Even if all conditions are met, you are also dependent on code updates from Phala, which you have no influence over.
Before starting
Before doing BIOS modifications, visit your vendor’s website and CHECK if there is a BIOS update. In many cases there will be one.
If not, then contact your vendor and ask for an updated BIOS. In most cases, the support will help you, but you must provide them with all the information needed. If you contact a vendor, then explain:
- You are using the SGX feature, which the Remote Attestation states vulnerable, listed as per the Intel SA’s. The SA numbers are listed in the SGX-test from the PHALA tool, so put them in your request!
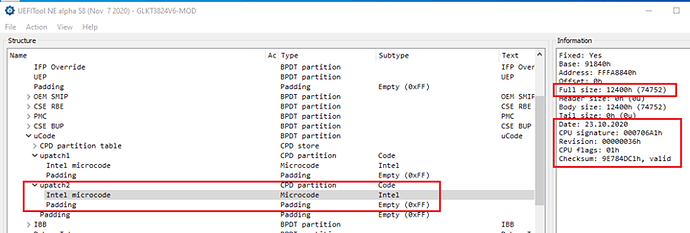
- You require a Micro Code Update, also known as MCU. Details on what an MCU is are listed in this document, but in short it’s a little file inside your BIOS that patches your CPU. It allows Intel to fix bugs; your vendor should know which MCU’s are correct for your motherboard.
- Explain that OS-level MCU patching (from Windows or Mac or Linux) does not work for Intel SGX. As Intel SGX is a security feature that an OS is unable to influence, so any MCU patching from within OS will not apply to Intel SGX features. The ONLY way to patch Intel SGX using MCU is loading it in the BIOS.
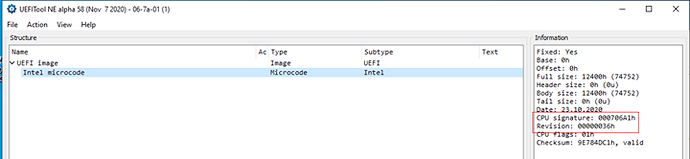
About Microcode
To put it simply: the Microcode is the software that runs the CPU. Some parts are always read-only (e.g. a serial number) while other sections are always writeable (e.g. changing boot order from your OS) … but the more tricky ones are both read-only or writeable, depending on what state your system is booted in. Intel SGX as a security feature should not be tampered with, as such it’s read-only after BIOS boot, but before BIOS is booted you can load a new MCU via a BIOS update, fixing Intel SGX problems. The MicroCode is also signed by Intel!
Updating the MicroCode (aka “MicroCode Update,” or MCU) can be done from two levels:
-
Loading it via the Operating System
This allows easy patching pf some problems from Intel, as it’s less invasive. For example, Spectre & Meltdown were patched in most cases from the OS. However, there is a limitation: not all CPU functions can be updated while once they have already started (like SGX). While the OS in most cases gets the latest MCU and loads it, it only applies to CPU features the OS can handle, so it does not solve your SGX problems. When you run a Secure Enclave in the CPU, it will use the MicroCode from the BIOS, not the OS. The OS cannot change the microcode used by the CPU for SGX; this is part of what system secure! When you ask your OS what MCU you are running, it will report the latest MCU, which is correct from the OS perspective… but this is false information from the perspective of SGX features. There is no good way to checking from the OS what MCU is loaded from the BIOS. -
Loading it via the BIOS
This allows full patching of all features, before control is handed over. It is the only good way for Intel SGX.
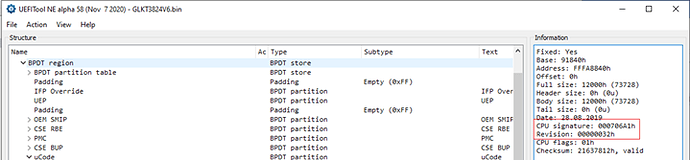
About BIOS files
To keep it simple, just think about your BIOS update file as a ZIP file. It contains multiple files (where the MCU is only a small part) to update all the items of your motherboard. All BIOS files since 2015 work the same way, but they contain hardware-specific configurations and only include what is needed for your specific hardware to limit space requirements. Because of this, BIOS files are not interchangeable, so if you download a BIOS file you must make certain it is for the motherboard you are using it for. Some (cheap) vendors may not have implemented any validation; they may allow you to flash an inappropriate BIOS file which might brick your system!